

Cyber threats change daily your defense must evolve as well. XLNC Technologies, a credible cyber security solution provider, equips businesses with agility, resilience, and security-first infrastructure.
From cybersecurity consultant expertise and cybersecurity consulting company guidance to end-to-end cloud security services, we safeguard your digital assets in every environment on-prem, hybrid, and cloud. As an innovative cybersecurity company and cloud security firm, we provide constant protection without trade-offs on performance.
Identified as one of the leading cybersecurity service providers, we deliver advanced cybersecurity solutions, enterprise cybersecurity solutions, and risk-reducing, compliance-enhancing, and operationally trust-building systems at scale. Whether looking for cybersecurity solutions provider support, cybersecurity tools, or enterprise-class SaaS, XLNC Technologies is your partner in secure digital innovation.
At XLNC Technologies, we provide end-to-end cybersecurity services designed to Protect, Detect, and Respond seamlessly:
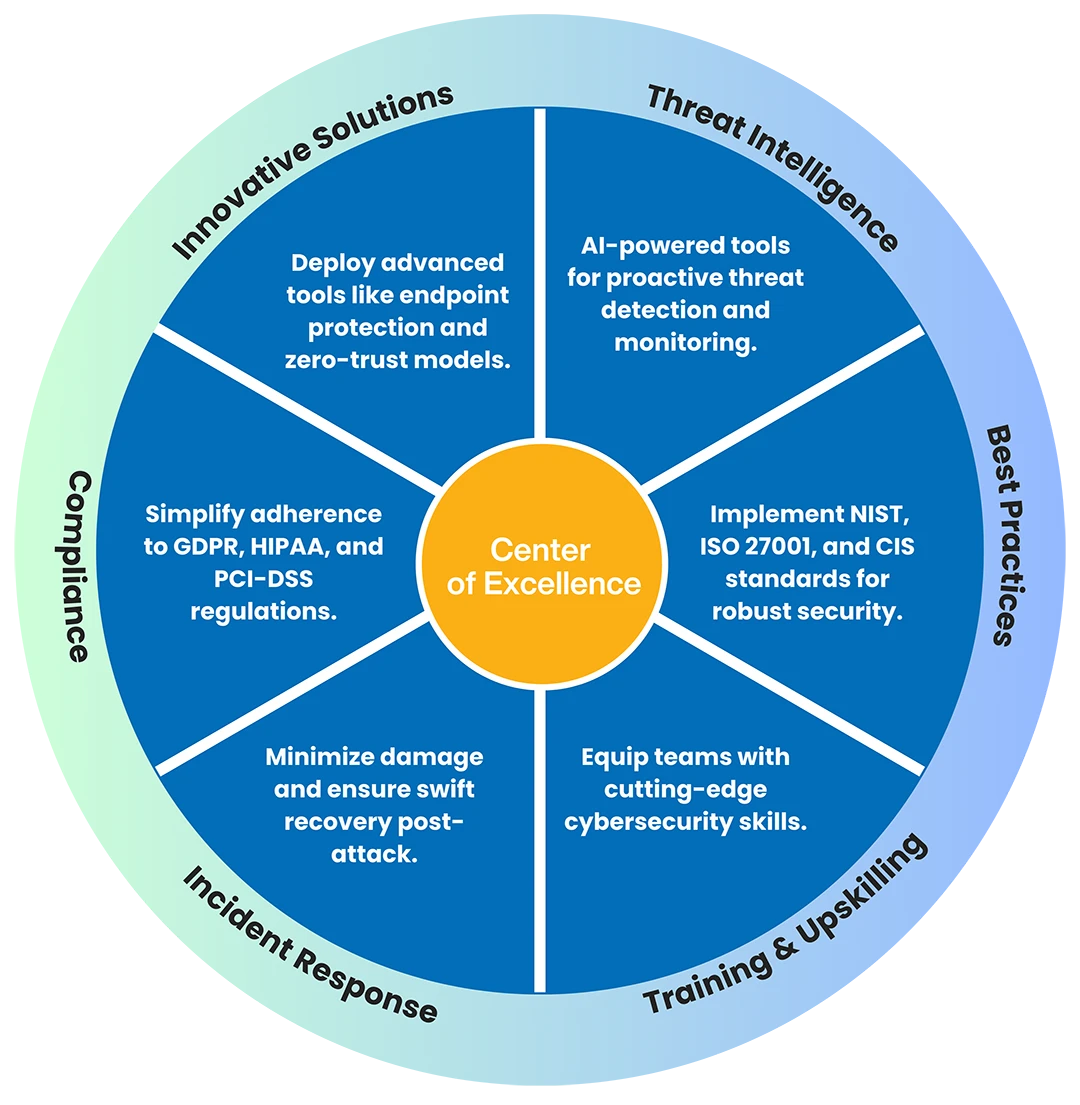
With AI-driven threat detection, 24/7 monitoring, and a Center of Excellence approach, our cybersecurity services provider team delivers smarter, scalable, and secure solutions.
Step 1: Assessment
Identify vulnerabilities through automated scans and expert cyber risk assessment and penetration testing.
Step 2: Implementation
Deploy best-in-class security measures, including endpoint protection, SIEM, IAM, and IT security solutions.
Step 3: Monitoring
Continuous 24/7 real-time monitoring and rapid incident response readiness.
Step 4: Optimization
Continuous IT Risk Management and compliance alignment with GDPR, ISO 27001, NIST, and CIS standards.
Step 5: Evolution
Adapt security frameworks proactively as threats evolve, with training, upskilling, and cyber defense strategies.
Benefits
of Our
CyberSecurity Solutions
Prevent data breaches and financial losses
Achieve and maintain regulatory compliance
Minimise downtime and maintain business continuity.
Build stronger customer trust and brand reputation.
Enable a scalable and future-ready IT infrastructure.
Boost operational productivity through secure access control.
Leverage AI-driven insights for faster threat detection.
Our solutions are customised to the unique threat landscape of each industry:
Trust is money in an industry where we safeguard each transaction, customer file, and digital asset with enterprise-level security. From securing core banking systems to maintaining regulatory compliance, our cybersecurity solutions assist financial services organizations in avoiding fraud, mitigating risk, and ensuring business continuity.
With increasing digital uptake and valuable policyholder information on the line, we keep insurers secure and compliant. Our cybersecurity solutions protect key systems against breaches, allow secure handling of claims, and promote customer confidence by actively reducing fraud and data leakage threats.
We protect patient information, clinical systems, and research assets from breaches and ransomware attacks. Our cybersecurity solutions provide HIPAA and international compliance, secure EHRs, and defend connected medical devices allowing healthcare providers to provide uncompromised care.
We safeguard student records, virtual classrooms, and online learning environments against data breaches and unauthorized access. Our cybersecurity solutions guarantee safe content delivery, uphold academic integrity, and deliver compliance-ready protection to institutions expanding digital education.
With a market powered by supply chain accuracy and time-sensitive coordination, cybersecurity is imperative for precluding data breaches, system downtime, and illegitimate access. We protect logistics platforms, fleet tracking systems, and partner integrations to enable secure, seamless delivery operations and strong supply chains.
As smart factories and networked equipment gain traction, manufacturing becomes increasingly vulnerable to operational interference and IP loss. Our industrial cybersecurity solutions protect industrial control systems, OT environments, and confidential data to keep production lines safe, productive, and running.
As customer trust relies on safe transactions and data security, cybersecurity is a crucial aspect in retail. We protect payment gateways, customer information, and back-end systems from hacks, fraud, and downtime to provide hassle-free, secure shopping experiences and brand reputation.
In an era of digital content and streaming platforms, cybersecurity is crucial to protect intellectual property, user data, and digital assets. Our solutions defend against piracy, unauthorized access, and service disruptions ensuring secure content delivery and seamless viewer experiences.
As more digital transactions, listings, and client data exchanges occur, the real estate industry is increasingly exposed to cyber threats. Our solutions protect sensitive financial information, ownership documents, and communication channels to provide safe, reliable property transactions and client relations.
In an industry with live data, digital properties, and user credentials flowing every minute, cybersecurity is paramount. We assist gaming platforms in preventing fraud, account hacks, and DDoS attacks for seamless gameplay, safe in-game transactions, and player trust across the world.

We offer VAPT, Managed Security Services, network security solutions, Endpoint Protection, and Compliance Support tailored for various industries.
Yes. Our scalable cybersecurity solutions are designed for businesses of all sizes, ensuring affordability without compromising cyber attack prevention.
To safeguard your digital ecosystem through assessment, protection, continuous monitoring, and rapid response to threats.
Real-time threat detection, compliance support, endpoint security, scalable cloud protection, and expert guidance.
By aligning security measures with industry standards like ISO 27001, NIST, HIPAA, GDPR, ensuring hassle-free audits and certifications.
Ready to safeguard your digital assets and fuel secure business growth? Contact XLNC Technologies — your trusted cybersecurity partner among the leading cybersecurity software companies and cloud security providers.